Fuzzing With Good Old Radamsa
“1337051nT”
“S3rlockedOSINTForall”
“oS$INTFOR@LL”
Did you know that Osint For All has many secret domain names? Just kidding, I don’t want to fuzz around any further, or maybe I do? So let’s jump in to the world of Radamsa.
Radamsa is a fuzzer. In technical terms, it is a test case generator for robustness testing. Typically, it is used to test how well a program could tolerate potentially malicious input. It works by reading files of valid data and generating random outputs every time from them.
Installation⌗
Prerequisites – gcc, git, make, wget. If you are on Debian based system just type:
sudo apt install gcc git make wget
The installation is pretty straight forward as the following.
git clone https://gitlab.com/akihe/radamsa.git && cd radamsa && make &&
sudo make install
Fuzzing⌗
Fuzzing is messing around a program by supplying it with vague inputs and see what happens. That’s where Radamsa comes into the play. Testers have a brief idea about what should not happen and they try to find that out. This referred to as negative testing, opposite to integration testing. Developers try to write programs which won’t crash, or consume lot of memory, whereas attackers try to crash the program and try to exploit it if its vulnerable.
Radamsa is more of a black box fuzzer, meaning it doesn’t need information about the program or the format of the data. It manages to break the data in into interesting ways as it flows through a program. Sometimes It could also generate more than one output.
Ways To Fuzz In Radamsa⌗
- Data through pipes
echo "Anaesthesia" | radamsa
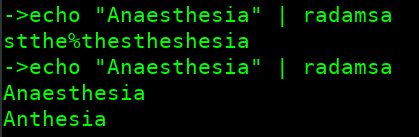
- Number mutator
echo "Anaesthesia 1337" | radamsa --seed 2
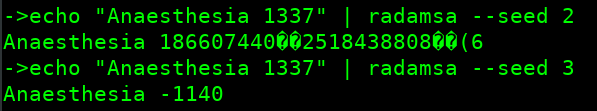
In the above example, Radamsa uses number mutation to change the textual numbers with something else.
- Multiple Outputs
Using -n flag, multiple number of outputs could be generated.
echo "Anaesthesia 1337" | radamsa --seed 8 -n 4
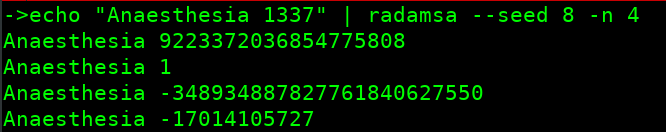
To learn more about different options, use the man page.
man radamsa
- Reading input from standard input
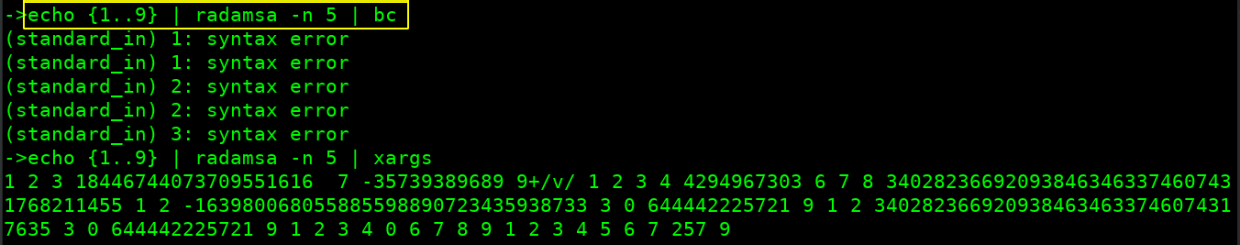
bc is a language that supports arbitrary precision numbers with interactive execution of statements. xargs is used to execute commands from standard input.
- cat out radamsa!
Let’s create a text file named l.txt and radamsit out and see if it could give us a random password!
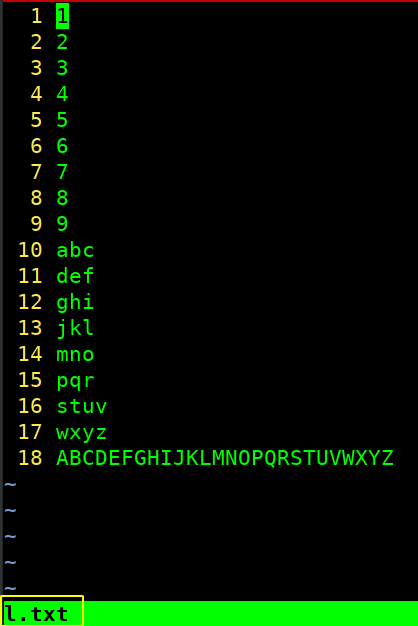
Above is the content of l.txt.
radamsa l.txt
After two iterations, radamsa generated a nice little string that could be used as a password.
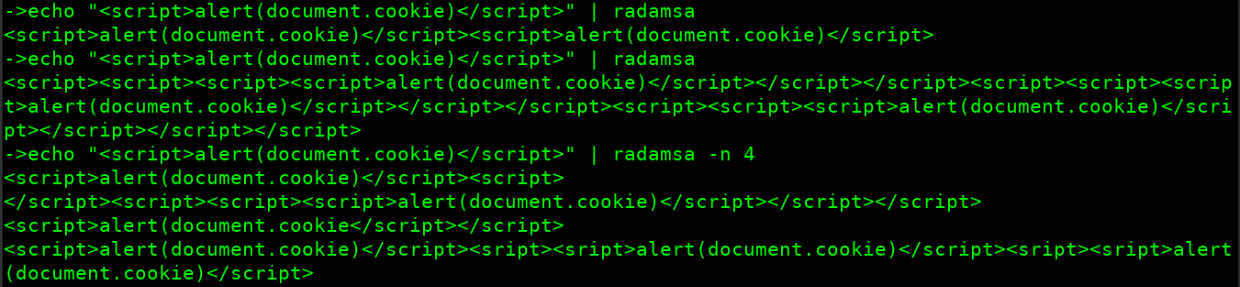
- Creating XSS payloads
- Fuzzing with different file formats
As aforementioned, Radamsa could take in almost any file format and give us a randomly generated string. So let’s compress l.txt to gzip and see if radamsa could give us the output.
gzip l.txt
radamsa l.txt.gz

Radamsa As A TCP Client⌗
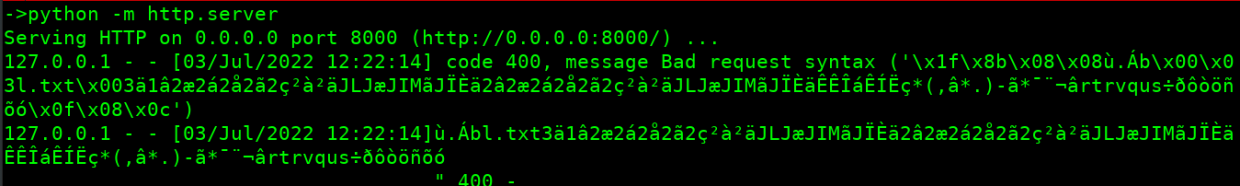
Radamsa is also capable of acting as a TCP client/server. So let’s start a simple python server see if radamsa could connect to it. And also let’s use the same l.txt.gz from the previous section as an input file.
python3 -m http.server
In another tab type the following.
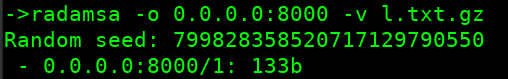
radamsa -o 0.0.0.0:8000 -v l.txt.gz
Output
Final Thoughts
Tampering with software and then seeing it break and misbehave is a delight to many hackers. Fuzzing is an art and Radamsa is one of the powerful tools to add to your hacking toolkit. Many CVEs have been discovered using Radamsa. Now go install Radamsa and fuzz the world!