OPSEC For OSINT CTFs
CTFs (Capture The Flags) are a great way to enhance your skills. Whether it’s information security or Open Source Intelligence based CTFs, at the end of the day, they improve your problem solving abilities, and also, they are fun!
I started this tradition of making Twitter threads during TraceLabs’s CTF about OPSEC, especially focusing on judges using LOW END COMPUTERS. So I thought why not make a blog post about it so that everyone could benefit. I’m also going to add some extra insights which I couldn’t cover in those threads.
Method 1⌗
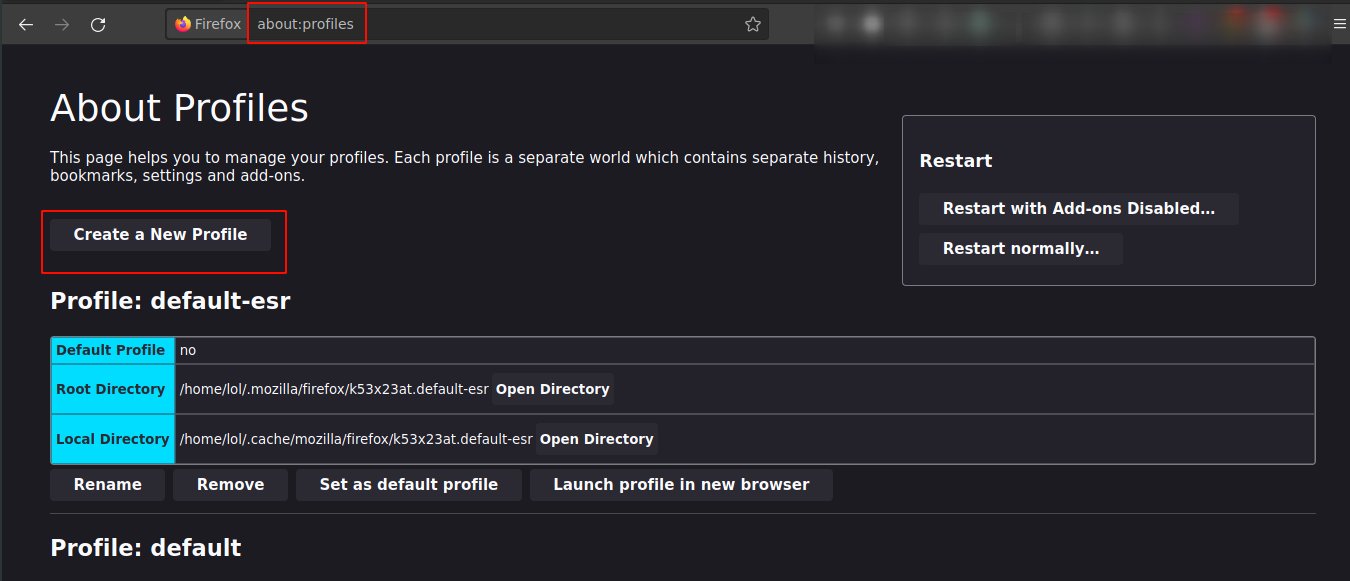
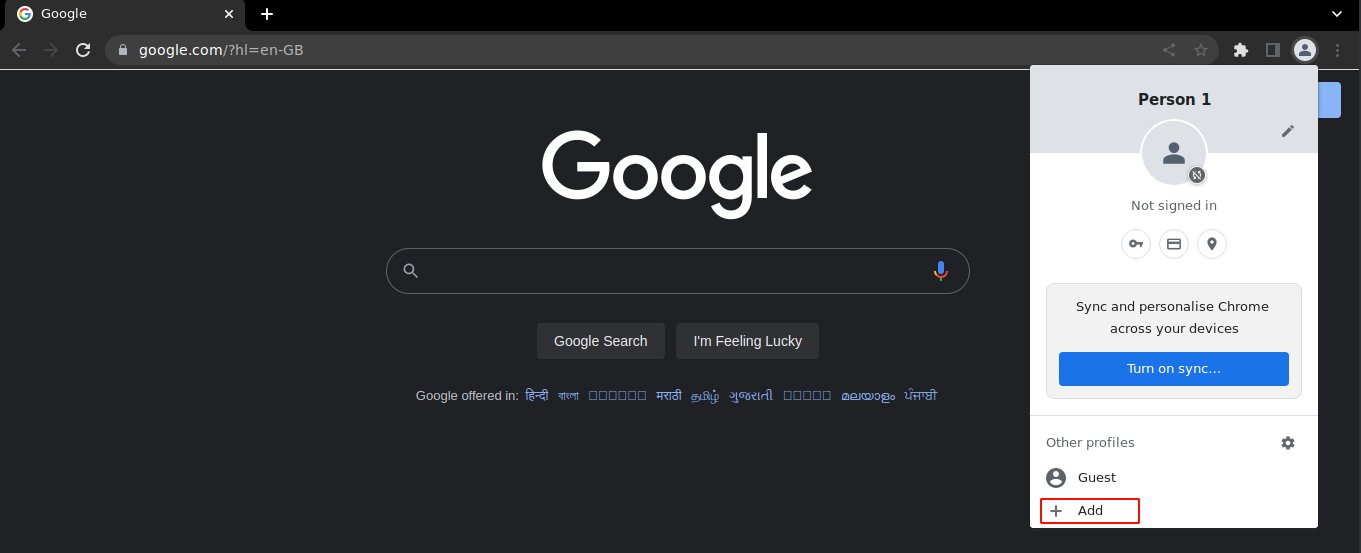
- Create a separate browser profile and delete it later. In Firefox based browsers, go to about:profiles and create one. In Chrome based browsers, you can find an option. And use User-Agent Switcher. Or you can also use Tor Browser(with/without a separate profile). Avoid installing addons or changing user agent strings while using Tor browser.
-
Use browser based VPNs within the profile. (Not recommending any VPN in particular, choose one by researching a bit on the web, or probably the ones with good ratings, maximum users and past records)
-
If available use ‘trustable VPN of your choice’ on your main machine, along with browser vpn. A better way to make sure that your VPN is not leaking DNS is to test at - http://dnsleaktest.com after setting up.
-
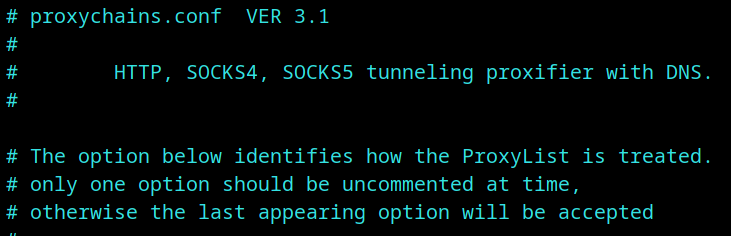
Use proxy chains (sudo apt install proxychains - for Debian based distros) and add public proxies down below in proxychains.conf, along with VPNs or use Tor proxy. Some privacy focused GNU/Linux distros, provide ‘anonymous mode’ or ‘tor mode’, use them.
Method 2⌗
Use Live/Persistent Bootable Pendrives
Live bootable pendrive runs live on your device, that means, when you pull the pendrive out of your system, all your data will be gone. To make it effective, combine it with the instructions from Method 1.
On persistent bootable pendrives, you can allocate some space for storage and also encrypt that space. You can save your data and settings on persistent pendrives. When you pull out the pendrive from the system, nothing will be stored on your system’s hard drive.
Recommended Operating Systems For Bootable Pendrives
- Tails (highly recommended)
- Kodachi OS
- Tsurugi
- Parrot OS
- Kali
FAQ⌗
What if I can’t create sock puppet accounts due to territorial restrictions and I can’t/don’t want to spend money on buying burners or temporary sim cards?
Ans: If the CTF is designed in a way, such that, you only need to verify the details of contestants' submissions, then, you don’t need sock puppet accounts; simply follow the instructions from Method 1 or use the Tor browser to do so. This applies only if the submissions are from social media platforms such as Facebook, Twitter, Instagram, LinkedIn, and so on; where you can view the content from a “shared link” unless it’s public. If any of the social media sites require you to login/signup for a second post from the same window, simply right-click on the link and open it in a private window, which will fool the link into thinking that you are a different person/session accessing the link.
Some Privacy Addons.
- User Agent Switcher
- Ublock Origin
- Privacy Badger
- Decentraleyes
- Disconnect
- Ghostery
- Facebook Container
Other Useful Addons
- Firefox Multi-Account Containers
- Session Box
You can disable Decentraleyes and Disconnect, if they block the javascript from the website that you want to access.
That’s all I got for today. This post will probably be updated once in a while. Keep learning.